Managing Resources Using Azure Resource Inventory and PowerShell – My Living Collection of PS Scripts
Introduction
Coming into a new Azure tenant as part of a new position or when engaging with a new client can be challenging. Often the environments are very complicated, containing different management groups, many many subscriptions, and 100s of resource groups across said subscriptions. An excellent way to get a comprehensive overview of all resources within an Azure tenant is to use the Azure Resource Inventory Report (ARI). The ARI was created by Microsoft Azure Engineers back in 2018 and is still a powerful tool for any Azure engineer today.
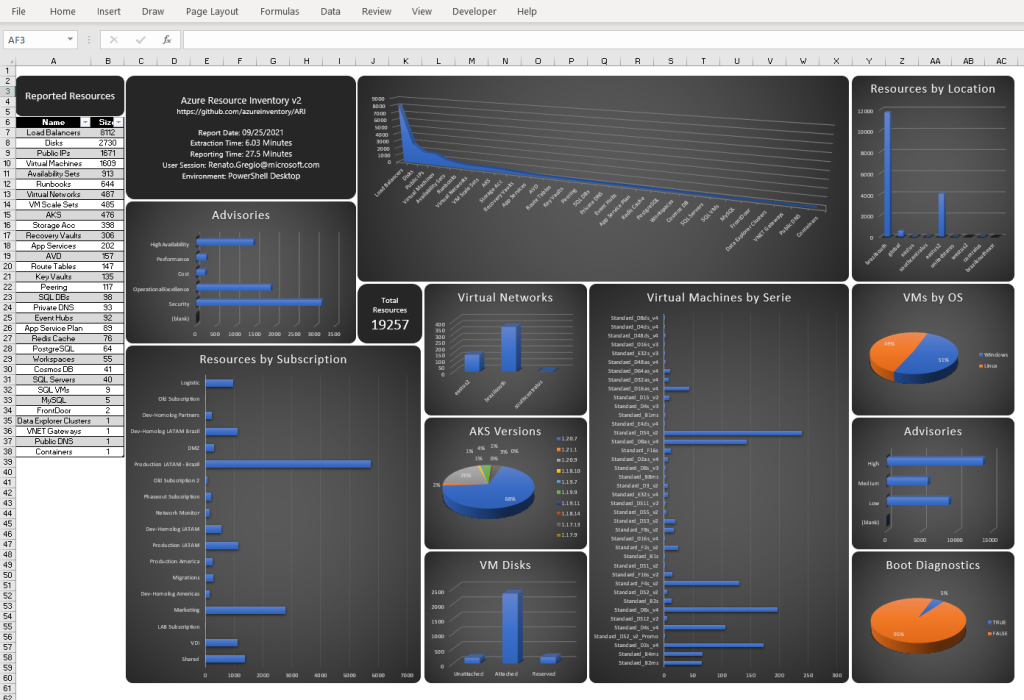
Information about the ARI can be found here.
By copying and pasting data from the ARI into a csv one can then create PowerShell scripts to do all sorts of fun things in Azure!
This post is intended to share the Azure resource inventory report and be a collection of PS scripts I have created to administer Azure resources from within a csv. I hope to update this post as I create new and relevant PS scripts.
Scripts:
Convert2GRS.ps1
A default configuration when provisioning storage accounts with the Azure portal is to enable RA-GRS. Due to this fact, many Azure tenants have this feature enabled and do not even need it. This feature gives the ability to read data from the secondary location of the storage account. RA-GRS storage account types cost more than standard GRS types.
The ARI has a sheet called “Storage Accounts” within this sheet is the “SKU” column.
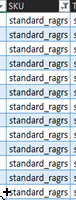
This script will log you into Azure, set AZ context based on subscription ID in csv, and set all storage accounts located in Convert2GRS.csv to Standard GRS.
How to run:
- Clone azure-powershell-csv repo to your local workstation.
- Input values into Convert2GRS.csv. Resource group where storage account exists, storage account name, and subscription are required.
- Change directory to Convert2GRS directory
- Run script ./Convert2GRS.ps1
- Choose preview (1) or live (2). Preview will run the script using -whatif and can be used as a test. Live runs the script and changes all storage account skus in Convert2GRS.csv to Standard GRS.
- Confirm storage account changes went as expected by verifying through the Azure portal.
DeleteListOfDisks.ps1
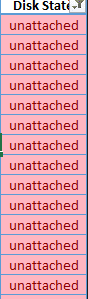
The ARI has an additional sheet “Disks”. Within this sheet, you can find all unattached disks in your Azure tenant. They will be highlighted in red. One can copy and paste unattached disk information from the ARI into a csv and use a PS script to delete them.
This script will log you into Azure, set AZ context based on subscription ID in csv, and delete each disk listed in ListofDisks2BeDeleted.csv.
How to run:
- Clone azure-powershell-csv repo to your local workstation.
- Input values into ListofDisks2BeDeleted.csv. Resource group where disk exists, subscription where disk exists, and name of the disk are required.
- Open a terminal to ListofDisks2BeDeleted.csv. directory
- Run script .\DeleteListOfDisks.ps1
- Choose preview (1) or live (2). Preview will run the script using -whatif and can be used as a test. Live runs the script and deletes all disks in ListofDisks2BeDeleted.csv.
- Confirm disks were deleted in the Azure portal.
DeleteListofAppSvcSSLCerts.ps1
Often times an Azure engineer will need to delete expired or faulty certificates from App Service Plans.
This script is the only one in the list where you will need to find another method to obtain the certificate thumbprint and subscription ID of the cert you want to delete because this information is not in the ARI. I hope to update this post in the future to include automation to detect expired App Service certificates.
This script will log you into Azure, set AZ context based on subscription ID in csv, and delete each App service managed certificate in ListofCerts2BeDeleted.csv.
How to run:
- Clone azure-powershell-csv repo to your local workstation.
- Input values into ListofCerts2BeDeleted.csv. Resource group where certs exist, subscription where certs exist, and name of certs are required.
- Open a terminal to .\DeleteListofAppSvcSSLCerts.ps1.
- Run script.\DeleteListofAppSvcSSLCerts.ps1.
- Choose preview (1) or live (2). Preview will run the script using -whatif and can be used as a test. Live runs the script and deletes all certs in ListofCerts2BeDeleted.csv.
- Confirm certificates were deleted in the Azure portal.